The Smart Home Market is Exploding with Internet Capability.
Only a few years ago, the only Internet-connected devices you might have in your home would be your computer and phone, and perhaps your television. These days, the “smart home” market is exploding with Internet capability embedded in a wide variety of appliances, equipment, and systems. Let’s have a walk through your home:
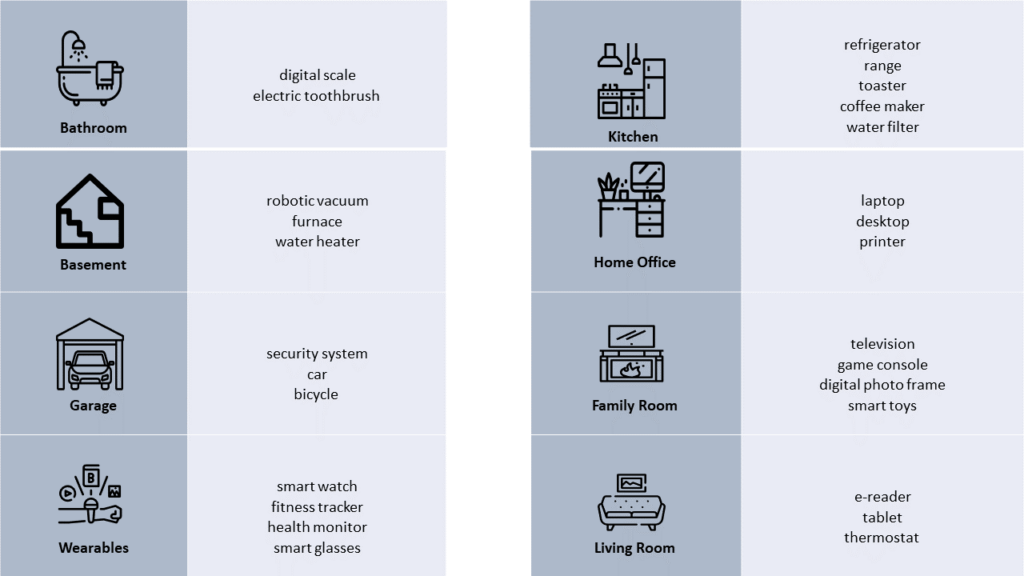
And this doesn’t even cover devices that could be in any room of your house, like smart home control systems like Amazon Alexa or Google Nest, smart lighting arrangements (equipped with smart bulbs, of course), door locks, cameras, carbon monoxide/smoke detectors, and even smart mousetraps! And a September 2019 report by IDC predicts even more and more connected devices are coming.
This smart home gear comprises a category of the so-called “Internet of Things” or “IoT”: devices that can connect and communicate on the Internet without human intervention. These devices can bring a lot of entertainment, convenience, and personal safety to your home. But, like anything on the Internet, there is a darker side that is important to understand.
The Risks
Each device can give an intruder a way into your home network. This introduces a variety of risks:
- your personal private information, passwords, personal activities and conversations could be exposed
- hackers looking to cause mischief could, for example: shut off your fridge, turn up your thermostat, trigger false security alarms, or place fake Amazon orders from your Alexa Echo
- more sinister, compromised devices can be used as launching points for hacking so-called “botnet” attacks, in which someone takes control of your devices and uses them to attack other targets, slow down or crash services or websites, or even mine cryptocurrencies.
The Defenses
There are some basic steps that you should follow to minimize the cyber risk involved with smart technology:
Home Wi-fi: Be sure to change the default name and password of your home network. Strength of signal means your neighbours and passersby can likely see your network, as you can see theirs: don’t reveal any personal or device information in naming the device/network. Consider setting up a separate “guest” network if your equipment supports this. Don’t be misled by the name: the guest network should be just as secure, but you can use it to isolate one-off IoT devices from your main network consisting of your home computer, printer, and storage. This way, in the event of a security breach, you have one extra layer of defence. This also keeps your most sensitive information segregated from visitors who may request access.
Take inventory: Take an inventory of the Internet-enabled devices in your home. Use the chart above as a guide, but also use your home Wi-fi system to identify other devices that may be connected to your network. Make sure to review the listing occasionally to keep it up to date. Many home Wi-fi management systems allow you to control/block which devices are connect to your system: if you cannot specifically account for a particular device, disable it to reduce your risk.
Take control: Now that you know what’s connecting, reflect on whether you really need the device to connect at all. The home security system? Sure. Your electronic toothbrush? Maybe not. Also consider using time-of-day controls so devices are only accessing the Internet when necessary. Shut off devices that are not in use.
Change default settings: As mentioned in the Wi-fi section, many devices come out of the box with a default name that may identify the type of device or location.
- Change this to something unique that you will recognize, without disclosing its name – or yours.
- Make sure that all passwords are changed from the factory settings (some devices ship with no password at all, or with “password” or “admin” as a default). Make sure the passwords are sufficiently complex, and unique. If one is breached, you don’t want all the rest of them breached too. And don’t use your address: after “password”, your surname, street name and street number are the next most obvious passwords for a hacker to test.
- Devices may also have hardware or software settings that share usage, location, or other personal information. Assess whether you want to share this information, and disable any sharing you don’t consent to. This can usually be done through an app accompanying the device, or by using a web browser to connect to the device. Consult the user manual or online help for each device before installation.
- Be sure to save the configuration changes. Reboot the device and confirm that all of the settings are “locked in” in case of power failure or battery replacement.
Choose wisely: Carefully research any new products that you are considering. Read independent online reviews. Choose companies that place an emphasis on privacy and security, and that offer control over passwords and security settings. It’s easy for vendors to add Internet access to just about anything, and declare it a “feature”. It’s more effort for the vendor to provide tested and reliable security with the device.
Routine Maintenance: Like your computer or phone, smart home devices will periodically get routine bug fixes and security patches. Keep your devices up to date. Many devices have auto-update features – consider if this is right for you. Make this part of your inventory process – review the devices, disable inactive units, patch active devices and consider password changes.
Be Aware: your smartphones and smart home devices are always listening to you, awaiting your next instruction. While this may offer some convenience, understand that some of these devices will record and assess your personal conversations. Move or disable devices if you prefer for your discussions to remain private.
More and more devices are offering Internet capabilities. The advantages are exciting, but you should always proceed with caution.
[1] Chart icons made by smashicons, icongeek26, mynamepong, freepik, and kiranshastry from www.flaticon.com.

