Expert insights that will help make your cloud journey rewarding and safe
Most businesses today are undergoing digital transformation, recognizing that cloud technology can bring benefits like rapid deployment, flexible workloads, broader integrations, and other efficiencies to their operations. Companies that may have been hesitant to move to the cloud have found that the COVID-19 pandemic created a sense of urgency for them to adopt new business models… whether they felt ready or not. According to a Check Point (March 2022) 2022 Cloud Security Report, 98% of companies surveyed have moved some workloads to the cloud; in fact, 35% of respondents said that more than half of their workloads are cloud-based.
While this shifting landscape has presented great opportunities, it has also created potential risks. That same Check Point report revealed that 27% of companies surveyed had experienced a public cloud security incident in 2021. So how can you take advantage of the cloud without sacrificing security? We spoke with Ricardo Henry, CISSP ISSAP ISSEP CCSP, Practice Lead – Cloud and Network Security, ISA Cybersecurity, to get his insights on some of the key factors for success that he encourages organizations to embrace during their cloud implementations.
1. Set a Strategic Plan
An effective cloud strategy sees cloud transformation as a journey, not just a “project”. Having an over-arching plan and vision will help set the course for the transition. Without a big picture, having a series of disparate, one-off projects can create inconsistencies, conflicts, inefficiencies in deployment, and security gaps – devaluing the benefits of moving to the cloud.
Ricardo explains: “A clear strategy will outline the rationale behind the digital transformation, articulating the business benefits and impacts. The strategy should identify risksand risk mitigations. And the strategy must include clear objectives and success factors.”
The strategy must extend across the organization as well. “To be successful, a cloud strategy should involve team members right across the organization, not simply in IT,” Ricardo continues. “Using cloud technology can have transformative impact on the business, so finance, legal, compliance, operations, and HR as well as IT and security leadership should be involved. Board and ownership must be aligned with the strategy to help provide the vision and support – and financing – for the initiative.”
A thoughtful strategy will also include an analysis of the loads to be migrated. It is seldom advisable to merely port in-house applications to the cloud as is. Each organization has different sizes, priorities, performance requirements, and data transit requirements for each load. These corporate characteristics must be understood in terms of the impact that cloud operations might have. Issues of configuration, performance, utilization, and flexibility may drive change to the application loads themselves to operate in a more cloud-friendly or efficient manner.
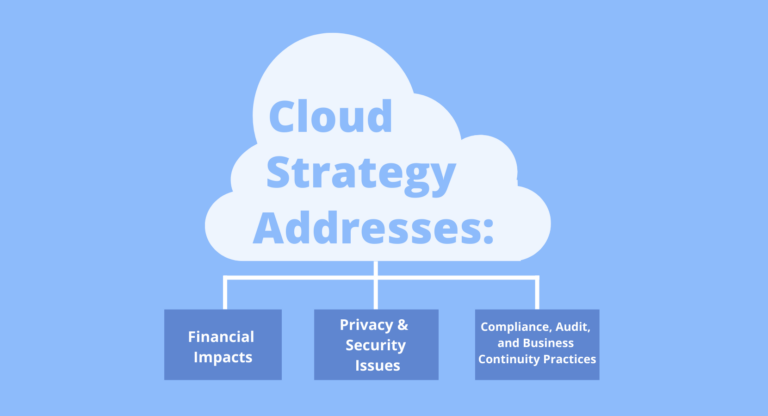
“Understanding the loads will also help define the scope of change – ranging from microservices and functions-as-a-service all the way up to using platform-as-a-service offerings,” Ricardo observes. “This understanding will help determine whether you go with a single cloud provider or go multi-cloud; whether public, private, hybrid, on-premises or edge cloud solutions are the best fit for each application or load. These decisions will drive operations and acquisitions. The cloud strategy will also address financial impacts, privacy and security issues (including data sovereignty), compliance, audit, and business continuity practices. Bigger picture, it will help shape the philosophy of the organization – should you be cloud-first or cloud-only? – so all of this should be thought through in advance.”
2. Authentication
It should be obvious that authentication is a critical part of securing a cloud infrastructure. But some organizations still haven’t implemented multi-factor authentication to secure their systems, or are still using traditional SMS two-factor authentication when more secure authentication apps are available to provide stronger protection. “Don’t even think about deploying cloud services unless you have a strong authentication policy in place,” Ricardo urges.
Most cloud servers have a variety of ways to connect remotely, such as RDP, SSH and web consoles. Organizations need to understand and identify all potential ways into their systems, and ensure they are locked down or turned off. Access must be audited regularly as well. A SIEM can be employed to alarm when unexpected connections are made.
Ricardo also flags a potentially hazardous area of authentication: administrator sprawl. “With more and more systems and services in play, it’s important to have thoughtful least-privilege access controls in place. Create separate admin accounts that are set based on your employees’ roles and responsibilities. The span of access of each admin account should be limited, and the number of admin accounts should be contained as well. This limits exposure.”
3. Posture Management
As Ricardo sees it, many companies have started their digital transformations to the cloud without taking a holistic view of security. “If you’re serious about making a digital transformation to the cloud, you really have to take a hard stop and think about how your company is going to operate with all of your assets in the cloud. Companies that simply lift and shift are running into problems: in order to have optimum cloud security, you need to utilize assets or tools from within the cloud to protect your infrastructure. One of the things a lot of organizations are missing on their journey is that they’re still trying to use on-premises solutions to protect themselves – and those solutions aren’t adequate.”
Ricardo recommends a cloud security posture management (CSPM) for getting the big picture of your cloud security environment. “Posture management tools help identify misconfiguration issues, gaps in security policy enforcement, and compliance risks in your cloud infrastructure. They follow best practices like NIST frameworks and PCI compliance. Just as with an on-premises vulnerability management solution, posture management is the recommended approach for ensuring your cloud infrastructure is secure.
“Consider something as simple as discovery. In a cloud environment, it can be very easy to spin up new databases and servers. A posture management solution can identify new loads, pinpoint configuration issues on those assets, and detect security loopholes. Your cloud infrastructure is always changing, and the threat landscape is always changing. There’s no practical way for individuals to keep on top of everything. These systems can identify – and, in some cases, even remediate – security issues before it’s too late.”
Each cloud service provides different capabilities for event logging and real-time visibility into performance and utilization of a customer’s environment. The added benefit of posture management is that it provides a single pane of glass for administration and monitoring. This is particularly important when multiple cloud providers are involved in the cloud deployment. Without posture management, companies with assets in AWS, Azure, GCP, and others are obliged to monitor each environment independently and attempt to correlate the data. With posture management, you can see exactly what workloads are doing with a holistic view of your cloud.
4. Don’t forget application security
Traditional approaches like network firewalls and MFA are important, but don’t provide the complete answer to protecting web applications and servers. The cloud ecosystem exposes systems to countless different tools and servers. It can be a complex architecture, and is quite unlike a traditional on-premises deployment. Modern cloud architectures are becoming more and more segmented and containerized, creating myriad opportunities for gaps in policy rules and permissions. A Cloud Access Security Broker (CASB) solution can be a security game changer.
CASBs can mitigate risk by enforcing rules between users, devices, and cloud instances. Ricardo explains: “It may be an over-simplification, but think of CASB as taking care of your SaaS deployments, while posture management solutions take care of your infrastructure-as-a-service environment. MFA is critical for authentication, but once you have established someone’s identity, you still need to know exactly what, when, where, and why they can access data or services. I don’t think all business appreciate the distinction, much less the potential complexities involved in getting it right – and the massive risks in getting it wrong.
“One of the biggest trouble areas I’ve seen is Office 365. There are great reasons for moving off on-premises Exchange and Office solutions. But simply porting everything to the cloud without MFA, without security and data access review, and without a solution like a CASB to prevent over-sharing of data is a real problem. It’s almost inevitable that data is going to start to leak out. Reflecting on the right security framework needs to come before the move to the cloud, not after.
I understand why companies don’t think about deploying a CASB if they’re simply moving to Office 365. To have a CASB for just one application might be seem overkill. But as your company’s cloud adoption grows, and you get more applications that are supported, that’s where CASB starts to shine. It lets you have one rule set that encompasses all of your data loss prevention and all of your security controls.”
Need advice on the right CSPM and/or CASB provider? ISA Cybersecurity can help.
5. Cloud Governance
As discussed, the ease of creating or using resources in the cloud makes it easy to create security risks. Companies should have a structured and documented process for spinning up new servers, services, and storage containers. Malicious attackers constantly scan for access to any open assets and will seek to exploit anything left accessible. System configuration changes, security rules, patch management: everything needs to be considered, otherwise it becomes a potential area of vulnerability. Having technologies like posture management and CASB are important, but having good governance over deployment is just as vital to maintaining strong security and optimal operations.
Companies also create security holes by leaving open ports and protocols that aren’t necessary. A least-privilege approach here reduces risk: start with no server access, then only add the ports and protocols that are required for the service to function. “Hardening” systems and reducing the attack surface limits exposure to both known and unknown threats to the environment.
Ricardo also reminds us not to forget about this issue in development environments: “While production may come close to a one-server-one-service orientation, DevOps teams may find it expeditious to implement multiple workloads on a single virtual system, and broaden security settings to accommodate this work. This can create unexpected security weaknesses, and allow attackers to breach and pivot if things are not adequately segmented and locked down.”
6. Don’t underestimate complexity
Migration to the cloud can seem deceptively simple: cloud providers can tantalize you with the ease of deployment, placing an emphasis on doing it fast as opposed to doing it right. There are many ways to go wrong from a configuration and security perspective. Cloud skills are scarce, and it’s costly and time-consuming to attract, hire, and retain top talent. Ricardo urges pre-planning: “Before you get too far down the road, consider whether you have the resources in-house, whether you need to staff up, or if it makes more sense to partner with experts to assist with the design, deployment, and maintenance aspects of your cloud transformation. Without a solid foundation, chances are your journey won’t be as successful.”
Part of building your cloud team is defining roles and requirements. Organizations can develop a bit of over-confidence with cloud services. Outsourcing services or infrastructure to the cloud doesn’t mean you aren’t still ultimately responsible for the data within those cloud services. It’s crucial to understand where your cloud provider’s responsibilities end, and where yours begin.
Ricardo provides examples: “Take software-as-a-service. With SaaS, the provider is responsible for providing an application and making sure it’s available for use when you need it. However, appropriate use of the application still resides with the customer. If that provider were to be compromised, have you implemented encryption on your data? Have you made sure your permissions and access controls were properly configured, your PCI compliance and data retention policies were being followed, and so forth. Companies must still recognize the responsibility for safeguarding their data, even if it’s residing on a cloud service.
“Let’s take another example with infrastructure-as-a-service. Just because you have cloud-based servers doesn’t mean that they will automatically apply patches or update themselves to the latest versions. Be sure that you have clear understanding of what the cloud provider is responsible for, and make sure you have some mechanism for auditing that work. Leverage your posture management service to keep abreast of emerging exposures and new versions. Understand that maintenance windows are essential, so design your resilience around knowing that systems will need to be down periodically for upgrades and patching. Cluster critical systems to share loads; have tested rollback procedures in case of problems.
“Another area where I see organizations underestimate complexity is in the use of multiple cloud providers,” warns Ricardo. “This is an area where it’s particularly importance to have the right strategy and the right skills.” While it may be more convenient to stick with a single cloud provider, many organizations are adding services from a variety of partners. There may be good business reasons to do this: best-of-breed services, financial incentives, integrations, and so on. But as challenging as it can be to manage the services from one provider, that complexity is multiplied when there are several platforms to configure, network, and administer together. “When you start leveraging several different providers, this often creates a huge skills gap as you need experts who understand the nuances of each environment as well as the interplay between them. Those are rare skills, and most organizations I’ve seen don’t have those capabilities in-house,” concludes Ricardo.
Make your move to the cloud safe and successful
Ricardo and the team at ISA Cybersecurity would love to speak to you about your cloud transformation. To learn more, contact us today. You’ll discover that ISA Cybersecurity has services and people you can trust.

