Six weeks after Wannacry ransomware, the Petya variant hit parts of USA and Europe. Although Petya is well-known, a new variant is now out in the wild.
How this ransomware works:
- Utilizes and modifies the Microsoft Windows SMB and uses the ETERNALBLUE exploit tool.
- Same exploit tool that was used for the Wannacry ransomware.
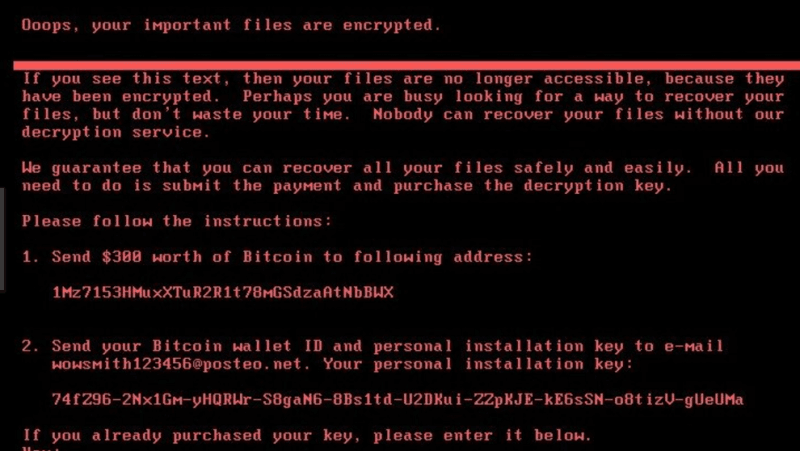
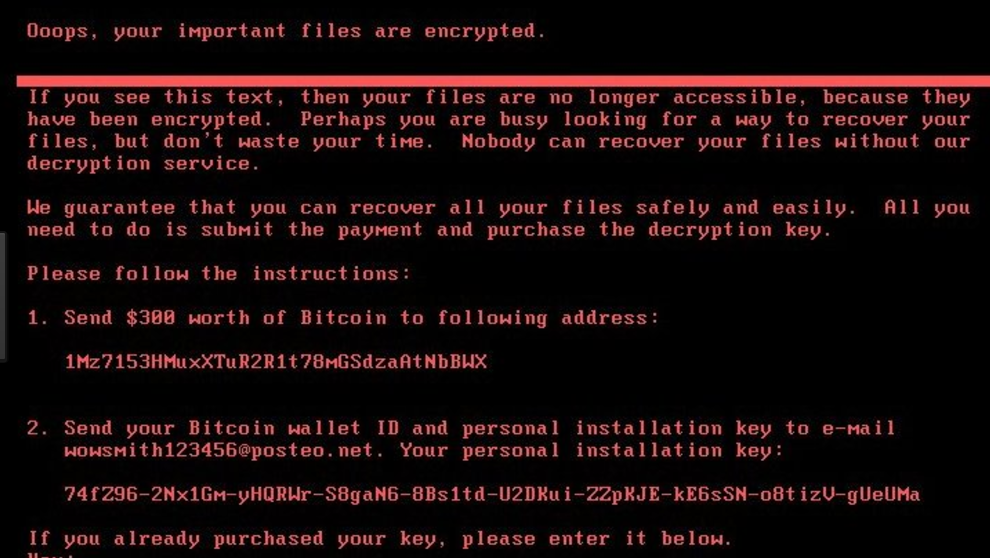
- Once infected, the MBR prevents Windows from loading into the O/S and a ransom
note is then presented to the end-user:
How to protect your systems:
- Windows systems should be patched with the March 2017 and April 2017 bulletins – specifically Microsoft Security Bulletin MS17-010
- Ensure all Anti-Virus signatures are up-to-date.
- If you have Advanced Malware Protection, you may already be covered.
- Some AV vendors may have a specific zero-day Petya update and should be distributed to all systems.
- If possible, block TCP 445 inbound.
- Create backups – in case of infection you can quickly restore data.
ISA’s MSP Services:
- Notified all customers at 12:30 PM EST on June 27, 2017.
- Assisting customers with zero-day protection.
- Continuing to monitor customer environments.
Additional Information
For McAfee customers, please follow these links:
https://kc.mcafee.com/corporate/index?page=content&id=KB89540
https://kc.mcafee.com/corporate/index?page=content&id=PD26470
For Fortinet customers, please follow this link:
https://blog.fortinet.com/2017/06/27/new-ransomware-follows-wannacry-exploits
For Cisco customers, please follow these links:
http://blog.talosintelligence.com/2016/10/mbrfilter.html
https://www.talosintelligence.com/mbrfilter
For Palo Alto customers, please follow this link:
https://researchcenter.paloaltonetworks.com/2017/06/unit42-threat-brief-petya-ransomware/
For additional information regarding this issue, follow this Virus Total link:
https://virustotal.com/fr/file/027cc450ef5f8c5f653329641ec1fed91f694e0d229928963b30f6b0d7d3a745/analysis/
Update – June 29, 2017
ISA is following the Petya/NotPetya Ransomware attacks. Find out more information below
http://heavy.com/tech/2017/06/notpetya-petya-ransomware-attack-virus-patch-petrwap-victims/
ISA is available to assist in any way possible.
Contact ISA Support: 1-877-591-6711 option 1, support@e-isa.com, or open a support case online.