Be your company’s cybersecurity hero.
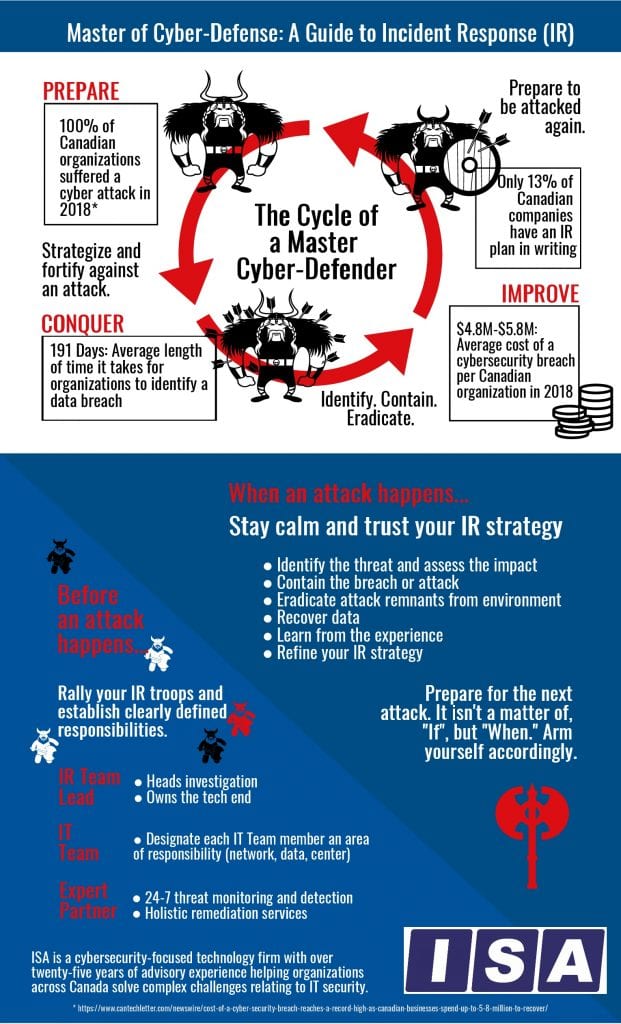
You don’t feel like a hero? That’s ok. Most heroes come from humble beginnings. Be assured; you can be a cybersecurity hero by mastering the art of cyber-defence. It all comes down to your incident response (IR) strategy. An incident response strategy has a three-part recurring lifecycle. So, to become a master of cybersecurity defence means going through a similar three-part recurring cyclical process.
You must prepare.
This period of training and preparation is the time when, if you were in The Karate Kid, Mr. Miyagi would have you painting his fence, sanding his floors, and waxing his car. You do preparation activities even though you don’t quite see how they will help you win a fight. Same is true in cybersecurity defence. Your first step to incident response happens before a cybersecurity incident occurs.
You prepare your staff by giving them specific roles and areas to take charge of should a cybersecurity incident occur. Train them. Practice your parts. Go so far as to write out incident response procedures. Build your fight strategy.
You ensure your attack surface is minimal. You familiarize yourself with where the most valuable assets are stored and where your network endpoints are. You look for all cybersecurity vulnerabilities. Your strategy should be to bolster your weakest points.
You make sure all of your software security is up to date, and that adequate endpoint and network security tools are in place. Keeping current on updates and patches is a sound strategy and helps you build your best defence.
You employ a cybersecurity partner to monitor your network and help you build your incident response strategy. Daniel-san had Mr. Miyagi. You have ISA.
You must conquer.
Attacks and breaches will happen. The cybersecurity game is continually changing, and a company’s defence has to be right all of the time, while a hacker only has to be right once. The odds are not in your favour. Cyber-criminals are the Cobra Kai to your Daniel. They will keep trying to take your data, and you won’t win every fight. However, if you’ve prepared, if you have a robust incident response strategy, then you will win when it matters most.
When the battle commences, remain calm. You’ve partnered with an expert security services provider, and they have your back. Your team will follow the directives you’ve already clearly outlined for them. You locate and then contain the threat quickly, because you know your environment, and have a small attack surface. Then you kick the enemy out of the system, eradicating all evidence of them. Networks are reinstated. Data is restored.
The damage was kept to a minimum because you were prepared with an incident response strategy and an alliance with ISA, a security solutions provider with a track record of excellence.
You must improve.
You return to the start. If this were an actual hero’s journey, you would return to the small village a better, stronger version of the warrior that left. Think of your organization’s network as your village. You may be bruised and battered from the cybersecurity battle, but you had prepared well, your incident response strategy was sound, and the damage was minimal. Your organization and your network will heal.
The cyber-battle still rages elsewhere and being attacked again is almost guaranteed.
So, the cyber-defender begins at a better beginning by returning to cybersecurity preparations. It isn’t full circle to go back to preparing because you now have a new way of seeing your environment, both its strengths and vulnerabilities. Begin to train again, while looking for new enemies, and strengthening your IR strategy. In Karate Kid II, Daniel and Mr. Miyagi are in fighting shape, physically and mentally prepared to take on new bullies and old grudges. Prepare for your sequel.
You need to commit to cybersecurity and incident response strategy fully. As Mr. Miyagi said, “Either you karate do ‘yes’ or karate do ‘no.’ You karate do ‘guess so,’ squish!” If you don’t have an incident response strategy in place, you risk getting squished.