Follow ISA Cybersecurity on LinkedIn for the latest cybersecurity news
Weekly CyberTip: Fake Recruiter Texts
A spate of bogus communications purporting to come from reputable recruiters is making the rounds. The source of the texts should tip you off that they aren’t real: they’re coming in via SMS text.
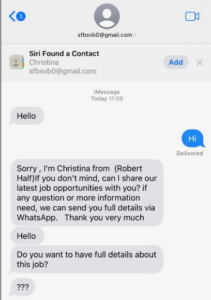
Unsolicited texts have been reported in a number of jurisdictions. Refer to the image below for a sample, which bears a number of red flags indicating that the message is fake:
- despite coming from a recognizable recruitment firm, the sender’s email address is a gibberish Gmail account
- the recruiter’s name is in brackets, suggesting that it may have been inserted into the message “mail-merge style” as a form letter
- the haphazard spacing, numerous grammatical errors, and unprofessional and unwarranted urgency of the message also indicate that the note is not from an authentic source
Be cautious about unsolicited job references, particularly over channels like SMS. Real recruiters should show more formality and precision in their communications. Independently vet any details before you act, and be especially wary of recruiters who request personal details or a recruitment fee early in the process.
Pilots’ union provides update on cyber incident
The Allied Pilots Association (APA), the largest independent pilots’ trade union in the world, took to X (formerly Twitter) on November 4 to announce that the “majority of our functionality has been restored” after a cyber incident on October 30.
In a November 2 update, they confirmed that the incident was ransomware-related, and that some of their systems had been encrypted. “As a result, the restoration of those systems has entailed a methodical and time-consuming process for our IT team and outside experts,” according to the update. The APA has warned users that they will have to set up a new password upon their first login on the restored systems.
The main APA website remains silent on the incident, though they have set up a dedicated website addressing FAQs, providing contact information, and delivering updates about the incident and the APA’s recovery efforts. The APA has not yet disclosed details about the nature of the incident, whether members’ personal information has been compromised, or the exact number of individuals affected. According to their website, the APA represents 15,000 American Airlines pilots.
SolarWinds exec charged with fraud
IT and security execs take note: the U.S. Securities and Exchange Commission (SEC) has announced charges against the SolarWinds Corporation and its CISO, Timothy G. Brown, for “fraud and internal control failures relating to allegedly known cybersecurity risks and vulnerabilities,” according to an SEC press release on October 30.
The complaint alleges that, “from at least its October 2018 initial public offering through at least its December 2020 announcement that it was the target of a massive, nearly two-year long cyberattack, dubbed SUNBURST, SolarWinds and Brown defrauded investors by overstating SolarWinds’ cybersecurity practices and understating or failing to disclose known risks,” also alleging that SolarWinds “misled investors by disclosing only generic and hypothetical risks at a time when the company and Brown knew of specific deficiencies in SolarWinds’ cybersecurity practices as well as the increasingly elevated risks the company faced at the same time.”
The complaint alleges that SolarWinds’ “public statements about its cybersecurity practices and risks were at odds with its internal assessments,” citing incidents suggesting that SolarWinds staff were aware of security deficiencies, but chose not to act.
While none of the allegations has been proven in court, the charges are a clear signal that the authorities are prepared to hold companies – and even the individuals in charge – to account if they fail to be transparent and responsive in the face of cybersecurity vulnerabilities.
BlackCat ransomware gang threatens to leak Henry Schein healthcare data
On November 2, the BlackCat ransomware gang (also known as “ALPHV”) added U.S. healthcare giant Henry Schein to its dark web leak site, claiming responsibility for an October 15 attack, and that they had stolen over 35 terabytes of sensitive patient data.
According to a report in Bleeping Computer, BlackCat also “claims they encrypted the company’s devices again just as Henry Schein almost finished restoring all its systems,” quoting the hackers as saying: “Despite ongoing discussions with Henry’s team, we have not received any indication of their willingness to prioritize the security of their clients, partners, and employees, let alone protect their own network.”
The hackers also threatened to disclose “a portion of [Henry Schein’s] internal payroll data and shareholder folders will be published on our collections blog. We will continue to release more data daily.”
The threat may have worked, as the entry on the leak site was deleted soon afterwards. Meanwhile, the investigation and recovery efforts continue at Henry Schein, whose primary order-taking websites remain down weeks after the initial incident. According to their investor site, Henry Schein employs 23,000 staff worldwide, serves over one million customers, and offers over 300 solutions for medical, dental, and even veterinary facilities.
Hackers leak data after southwestern Ontario healthcare cyber incident
On November 2, the organized cyber criminal gang called Daixin Team claimed responsibility for stealing millions of records from five southwestern Ontario healthcare facilities. After authorities refused to accede to their ransom demands, the group has now leaked two sets of sample patient data on the dark web.
The incident started on October 23 when TransForm Shared Service Organization was compromised, leading to cyber incidents at Bluewater Health in Sarnia, the Chatham-Kent Health Alliance, the Windsor-Essex hospice, Erie Shores HealthCare in Leamington, Windsor’s Hôtel-Dieu Grace Healthcare, and Windsor Regional Hospital – all serviced by TSSO. The healthcare facilities remain without access to some of their systems, with patient care at risk in some cases. In the early days of the attack most of the hospitals’ computer systems were down, including Wi-Fi, email, and patient information systems.
Local police departments in each area, the Ontario Provincial Police (OPP), the FBI, and INTERPOL are assisting in the continuing investigation into the incident.