Follow ISA Cybersecurity on LinkedIn for the latest cybersecurity news
Bed Bath & Beyond discloses cyber incident
On October 28, international home goods chain Bed Bath & Beyond (BB&B) disclosed that one of their staff had fallen victim to a phishing attack, exposing information to a threat actor. According to a Security & Exchange Commission (SEC) filing regarding the matter, BB&B said that the outside party had accessed “data on the hard drive and certain shared drives to which one of its employees had access. The Company is reviewing the accessed data to determine whether these drives contain any sensitive and/or personally identifiable information. At this time the Company has no reason to believe that any such sensitive or personally identifiable information was accessed or that this event would be likely to have a material impact on the Company.”
Coincidentally, it was almost three years to the day since BB&B disclosed another security breach, when an October 2019 incident saw an unauthorized third party gain access to email and password information for a small segment of the company’s customer base.

Internet Explorer still causing security issues months after being officially retired
On October 25, researchers at Varonis published a report documenting that persistent event logs from Internet Explorer (which was officially retired and out of support on June 15, 2022) could still create significant security risks. In their report, the researchers detail two different ways in which a threat actor could leverage information in the security logs to potentially exploit a machine. “These exploits (LogCrusher and OverLog) both use functions of the Microsoft Event Log Remoting Protocol (MS-EVEN), which allows for remote manipulation of a machine’s event logs,” wrote the Varonis team.
The researchers reported the issues to Microsoft, who provided a “partial patch”. While “Microsoft has opted not to fully fix the LogCrusher vulnerability on Windows 10 (more recent operating systems are unaffected),” according to the report, in “Microsoft’s October 11, 2022 Patch Tuesday update, the default permissions setting that had allowed non-administrative users access to the Internet Explorer Event Log on remote machines has been restricted to local administrators, greatly reducing the potential for harm.”
The report observes that, “[w]hile this address [sic] this particular set of Internet Explorer Event Log exploits, there remains potential for other user-accessible application Event Logs to be similarly leveraged for attacks. We recommend that all potentially vulnerable systems apply the Microsoft-provided patch and monitor any suspicious activity.”

CCCS issues National Cyber Threat Assessment 2023-2024 report
The Canadian Centre for Cyber Security (CCCS) has released a formal report forecasting trends and themes in cyber risk to Canadian organizations in the coming years.
The report provides an excellent primer on current cybersecurity issues, concerns, and opportunities for improvement. The findings are also described in terms of five key themes expected to be prevalent in Canada’s cybersecurity landscape over the next two years:
- Ransomware is a persistent threat to Canadian organizations; almost certainly the most disruptive form of cybercrime facing Canadians.
- Critical infrastructure is increasingly at risk from cyber threat activity
- State-sponsored cyber threat activity from China, Russia, Iran, and North Korea is negatively affecting Canadians.
- Cyber threat actors are attempting to influence Canadians, degrading trust in online spaces, and Canadians’ exposure to misinformation, disinformation, and malinformation (MDM) will almost certainly increase over the next two years.
- Disruptive technologies like digital assets, machine learning, quantum computing are increasingly both targets and tools for cyber threat actors.
Microsoft issues “Raspberry Robin” warning
Microsoft has issued a warning about a sharp increase in the use of the so-called “Raspberry Robin” worm malware. According to their security blog, “Microsoft Defender for Endpoint data indicates that nearly 3,000 devices in almost 1,000 organizations have seen at least one Raspberry Robin payload-related alert in the last 30 days.”
The malware was originally devised to spread to Windows systems through infected USB drives (wherein the drive bore malicious Windows shortcut (LNK) files disguised as a folder. However, in recent months, Raspberry Robin “has evolved and is heading towards providing a potentially devastating impact on environments where it’s still installed. Raspberry Robin will likely continue to develop and lead to more malware distribution and cybercriminal activity group relationships as its install footprint grows,” according to the blog.
The blog post provides extensive technical details about the Raspberry Robin worm infection, along with preventative measures to take right away, along with a set of indicators of compromise to test in case systems are potentially infected already.
Australian healthcare sector company hit by data breach
On October 28, Melbourne-based Australian Clinical Labs (ACL) disclosed that they had suffered a data breach in February 2022 that had affected the Medlab Pathology arm of their business. Medical records and sensitive personal information belonging to over 223,000 people was compromised in the attack.
ACL’s official data breach incident notification explains the scope of the breach, which involves (in part), the following disclosures:
- 128,608 Medicare numbers, along with full names;
- 28,286 credit card numbers, 12% of which include CVV code, and 55% expired; and
- 17,539 individual medical and health records associated with pathology tests.
ACL is an Australian healthcare company that operates 76 NATA-accredited laboratories (including four central laboratories) servicing over 90 hospitals in all states and territories in Australia except Tasmania, performing some 8.3M tests annually.
Weekly CyberTip: Watch out for bogus refunds
This week’s CyberTip provides a real-life example of an SMS-based phishing (or “smishing”) attack, illustrating how they can appear convincing, but can lead to devastating consequences if you aren’t careful.
On Sunday evening, a member of our team received the following text message:
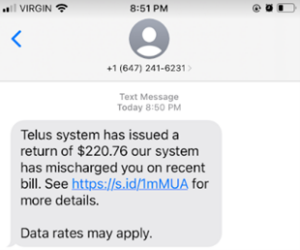
This would be exciting news, except for the fact that (as shown), the team member is on the Virgin network and is not a “Telus system” subscriber. Setting aside the grammatical errors in the text, we hovered over the link, noting that it would take us to “telusreturn.info”, a bogus site with a name devised to trick people by including the word “telus” in the domain.
Under controlled circumstances, we investigated the domain. First, we were challenged with an hCaptcha validation, giving the site an air of authenticity. We assumed it was just a coincidence that the phishing text asked us to validate by identifying fish!
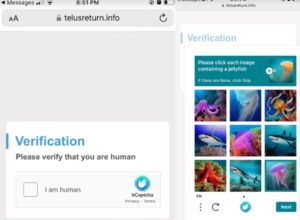
After clearing the verification hurdle, we were then prompted to accept an Interac e-Transfer, then asked to enter financial information. These pages were well-crafted and looked just like a real Interac transfer site.
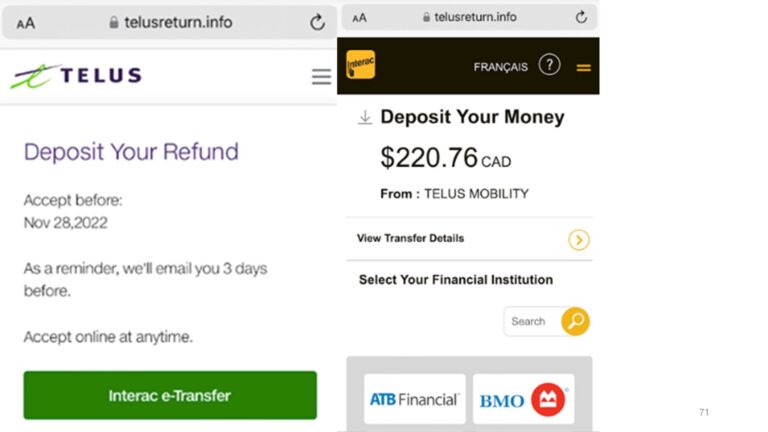
The test was discontinued at this point, but if account information had been entered, the threat actors operating the bogus “telusreturn.info” website would have collected the data, then pivoted to use the credentials to clear out the bank account – not deposit a refund into it.
The lessons here are to watch for awkward phrasing in communications, validate the URLs of any links, and if you receive a surprise communication about a refund (whether or not you do business with the organization), contact them directly through a trusted channel and avoid clicking on potentially harmful links.

