Follow ISA Cybersecurity on LinkedIn for the latest cybersecurity news
Weekly CyberTip: Beware of phishing texts
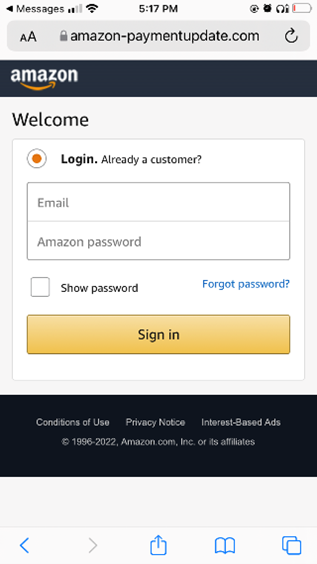
This week’s CyberTip is based on a real-life attack ISA Cybersecurity analyzed on March 6. Figure 1 shows an unsolicited text received to a mobile phone. Under controlled circumstances, we opened the link, as shown in Figure 2. Here, note the URL reads “amazon-paymentupdate.com” – a domain that seems authentic, but is actually a malicious site set up in late February 2022 in The Netherlands to trap unwary shoppers. The fake site even forces the victim to pass a reCAPTCHA challenge before proceeding, lending an air of authenticity to the attack. Figure 3 presents a “login page,” mimicking Amazon’s login page, but actually only set up to harvest your email address and password. If you enter your credentials here, you will be handed off to the real Amazon website… but your login information will have been compromised.
Always be suspicious of surprise alerts about service disruptions. Use web content filtering and check URLs carefully. When in doubt, contact the vendor through an independent source without clicking on links or attachments. Amazon provides a detailed page of tips on how to recognize, avoid, and report fraud attempts by text, phone, voice, or advertisement.
Figure 1
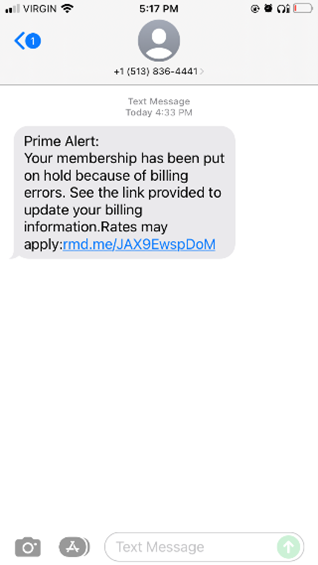
Figure 2
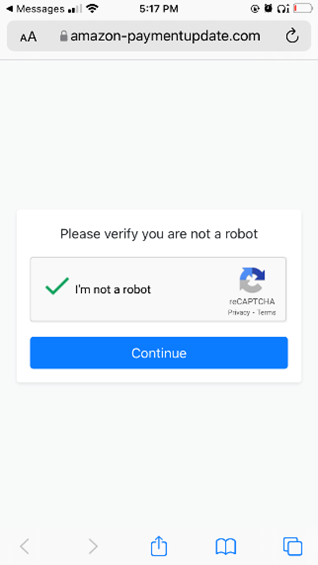
Figure 3
Ukrainian cyber firm offers bounty for hacking Russian targets
In the escalating cyber war between Ukraine and Russia, Kyiv-based cyber firm Cyber Unit Technologies has offered a bounty for taking down selected Russian targets. Cyber Unit has pledged an initial $100,000 USD reward pool, and is actively soliciting donations to increase the bounty. A full interview with an executive from the firm is available on cybersecurity news website The Record.
Cyber Unit has not disclosed whether any individuals have yet claimed a bounty.
Proofpoint identifies state-sponsored phishing campaign targeting European governments
In a March 1 report, Proofpoint reveals evidence of a state-sponsored phishing campaign against European government personnel that are coordinating Ukrainian refugee logistics. Nicknamed “Asylum Ambuscade,” the phishing campaign features emails bearing an Excel attachment containing a malicious macro designed to deploy “SunSeed” malware on a compromised computer.
The phishing attacks, which bear the hallmarks of known hacking attempts employed by the Russian military, were alleged to have come from a Belarusian state-sponsored hacking organization. “Researchers assess that this may represent a continuation of the campaigns that utilize compromised Ukrainian personal accounts of armed service members to target the governments of NATO members in Europe,” according to the report.
The attacks serve as a reminder of the importance of maintaining vigilance when receiving unexpected emails with attachments, even if the messages appear to come from a known or trusted source.

Ukraine joins NATO cyber group
The NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) has welcomed Ukraine as a “Contributing Participant”. Ukraine’s application was accepted with a unanimous vote among the 27 CCDCOE sponsoring nations that comprise the steering committee.
In a March 4 statement announcing the membership, the CCDCOE wrote, “Ukraine’s presence in the Centre will enhance the exchange of cyber expertise, between Ukraine and CCDCOE member nations. Ukraine could bring valuable first-hand knowledge of several adversaries within the cyber domain to be used for research, exercises and training.”
Ukraine becomes the group’s fourth “Contributing Participant,” a designation for non-NATO countries participating in the program. Austria, Finland, and Sweden are also Contributing Participants.
The CCDCOE is a NATO-accredited cyber knowledge hub and research institution. Based in Tallinn, Estonia, the organization focuses on interdisciplinary applied research, as well as consultation, training, and exercises in the field of cybersecurity.

Conti ransomware gang ceases operations
Capping a tumultuous week for the infamous hacking group, the Conti ransomware gang shuttered its back-end systems and command-and-control infrastructure on March 2. The Conti gang had come under fire from its affiliate members after declaring full support for the Russian government in the wake of the Russia’s unprovoked invasion of Ukraine in late February. Conti doubled down by threatening to mount attacks on critical infrastructure of any adversaries launching cyber attacks against Russia.
However, many of Conti’s affiliates are based in Ukraine, and their backlash was swift. On February 27, a Ukrainian researcher leaked data including over 60,000 internal messages from the Conti chat servers. The two months’ worth of discussions disclosed a “providing a treasure trove of information on the cybercrime organization, such as bitcoin addresses, how the gang is organized as a business, evading law enforcement, how they conduct their attacks, and much more,” according to a report in Bleeping Computer. Subsequent leaks disclosed source code, decryption keys, and other important Conti data.
While the disruption of Conti’s operations is a short-term positive, the disclosures may have a darker side as other ransomware groups may use the Conti framework and approach to develop their own malware variants.

New healthcare study from Palo Alto highlights IoMT vulnerabilities
In a March 2 report, researchers from Palo Alto Networks revealed that a scan of 200,000 infusion pumps in North American hospitals showed that 3/4 of those devices had known, unpatched security vulnerabilities.
According to the report, those “shortcomings included exposure to one or more of some 40 known cybersecurity vulnerabilities and/or alerts that they had one or more of some 70 other types of known security shortcomings for IoT devices”. The researchers found that just over half of the infusion pumps scanned were susceptible to two known key vulnerabilities (one critical, one of high severity) that were disclosed to the general public as early as 2019.
The report espoused four key strategies to secure IoMT (Internet of Medical Things) devices:
1. Accurate discovery and inventory: Having a detailed, current inventory of type and location of IoMT devices is essential.
2. Holistic risk assessment: Having an over-arching risk assessment and mitigation strategy is important to help security teams find and resolve vulnerabilities.
3. Apply risk reduction policies: the report emphasized that real-time monitoring, reporting, and alerting are crucial for organizations to proactively reduce IoMT risk and support zero-trust architectures.
4. Prevent Threats: The report acknowledged the diverse nature of IoMT devices, and that appropriate configuration and proactive threat detection and prevention is key in helping to mitigate risk.

