Even in today’s climate of constant threat of cyber attack, IT professionals may still encounter challenges in getting the cybersecurity message across to their board of directors. Here are some strategies for helping to raise visibility, awareness, and support for cybersecurity initiatives at your organization.
Preparation
While your exposure to the board may be limited to a few meetings a year, it’s helpful for you to understand the backgrounds of the members, the group dynamics, and the composition of committees and working groups among the executives. Identify board members who are tech savvy, those who are interested in learning more, and those who may tend to tune out anything technical. When new members join the board, be sure to learn about them and their backgrounds. Shape your message as appropriate for your audience.
When planning your engagements with the board for the year, it’s helpful to understand the over-arching board schedule. How often does your board meet versus the frequency of your presentations? What committees and sub-groups are operating that may have a particular interest in cybersecurity – risk and governance sub-committees are likely candidates.
Bigger picture, you must understand the business landscape and the over-all priorities of the board and your organization. Your request for funding or outline of plans for new cybersecurity initiatives are, no doubt, well thought out – framing these “asks” in terms of addressing larger threats faced by the company will help your presentation resonate with the board. Your presentation must be crafted to address organizational risk exposure areas and emerging threats faced by the company, and should implicitly align with the values and mission of the enterprise.
Presentation Content Elements
Most board members will not be tech experts, so they will be seeking confirmation of your credibility, and the soundness of your plans and strategies. Remind your audience that cybersecurity is a journey, not a destination. Your presentation should reflect an alignment with your overall cybersecurity strategy. Boards will want to have comfort that you are constructing a clear, comprehensive approach for preventing, identifying, and responding to cybersecurity incidents. New initiatives should clearly tie into your current cybersecurity plan, your IT strategic plan, and your company’s over-arching strategic plan. Explain how this year’s projects tie into a bigger picture of governance, risk management, and security controls.
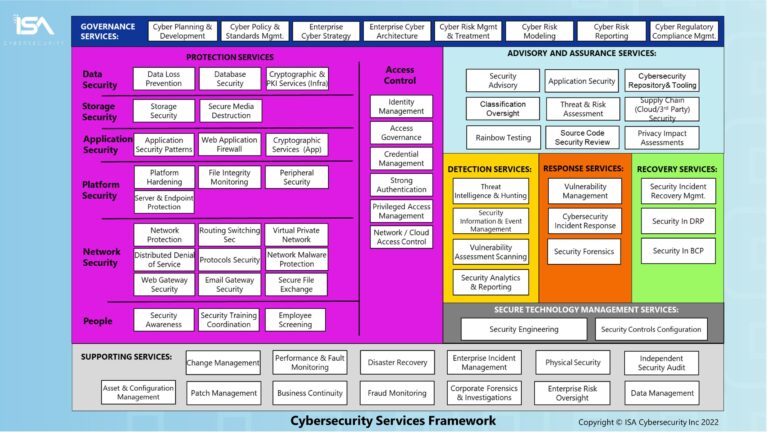
Consider the following cyber domain and service framework chart: where does your proposal fit in the big picture? Use illustrations to show your areas of emphasis and progress over time.
You can lend credence to your strategy by showing its alignment with industry standard frameworks. How does your plan align within the NIST cybersecurity framework, the CIS Top 20 controls, or the ISO 27001 ISMS? Further justify your strategies by explaining that your plans are required for PCI compliance, or your industry’s regulatory framework, or are needed to support essential cyber insurance underwriting requirements.
Many boards want to see that your spending proposals are in line with industry, national, or company-size standards. Leverage market research data or industry trade publications to identify these averages. Commonly used reference points include:
• security budget per year, per FTE
• security budget as a percentage of IT or corporate budget
• security budget as a percentage of gross revenue
• percentage increase/decrease of security budget over time
How does your proposal line up against these market benchmarks? What is your explanation if it is significantly higher or lower?
Define and present metrics that illustrate the performance and effectiveness of your existing security controls. Measures like downtime, time to detect/resolve/contain threats, number of phishing attempts reported, time to patch, etc. can help show where your security program is working effectively as well as objectively flagging areas that need improvement. These metrics and KPIs are even more compelling when tracked over time, as well as compared against industry benchmarks.
When proposals involve using third-party or managed service providers, be prepared to defend your choices: business partners with proven track records, decades of experience, and relevant industry expertise will give your board added confidence in your approach
Effective Messaging
It’s essential to steer clear of techspeak when addressing your board. While you may have a few technophiles around the table, it’s more likely than not that the group will have more business savvy than cyber knowledge. Understand this, and be sure that your messaging is defined in business terms and imperatives that will resonate with them. Emphasize that cybersecurity is not just an “IT issue”, but an essential business function and risk management strategy.
Boards may need to be educated on the threat landscape, and what dangers exist to the business. As you do when conducting a risk assessment, a compelling business case for a board will include identifying digital assets that are at risk, known and potential threats, and areas of vulnerability. Mapping these areas to the “risk appetite” of the enterprise will help create a call to action for making improvements to your cybersecurity defenses. The NIST heatmap approach can help your board visualize the areas of concern that you want to address. It can quickly illustrate where you’re strong, and where you need to improve, without getting overly technical. Your initiatives can then be presented in terms of risk management and business outcomes – not tech talk.
Your messaging should lay out timeframes, anticipated investment required, and your longer-term cybersecurity strategy. Where possible, it’s helpful to present an ROI backup for your ask, but it is often challenging to put a dollar figure on risk mitigation. Industry statistics of the costs, damage to goodwill, and business impacts of a cyber breach can be used as illustrations. And remember this messaging doesn’t always have to be negative: explain how improving your cybersecurity posture can deliver a competitive advantage or improve customer/staff satisfaction.
Make time to sit with your CEO and ensure that you are both on the same page with respect to presentation approach and content. The CEO will have valuable insights on the best ways to communicate with the board, and can provide tips on tone, form, and substance. If at all possible, run through your presentation in advance with the CEO and/or your supervisor to confirm understanding and alignment of vision. It’s essential to have confidence that the top executive will have your back during your presentation.
While it may not be part of your set presentation, it is often useful to have slides or materials prepared outlining your staff awareness programs, incident preparedness planning strategies, and broader approaches for managing cybersecurity programs and risk. As appropriate, illustrate how your plans will help foster organizational “cyber savvy”, will help make the company more nimble in the face of crises like the COVID-19 pandemic, will help the enterprise be ready to expand into new markets or exploit cloud technology, and so on. Be prepared to specifically address how your cybersecurity programs support audit and compliance, and how this year’s plan will further those initiatives. Have a slide outlining your approaches for in-house, cloud, or managed services for cybersecurity – and why you’ve chosen those strategies. Board members will naturally compare their own experiences (in business, or from what they’ve seen on other boards) and seek justification for your approach.
Your answers will give the board the confidence that you have things under control, and can be trusted with investment of time, money, personnel, strategic outsourcing, etc.
Presentation Day
Board agendas are usually packed, so your time at the table may be limited, shortened, re-scheduled, or even bumped altogether. Set yourself up for success by anticipating these different situations. Be sure to rehearse and time your presentation to align with the time you’ve been allocated, but have an “express” version of your slide deck or remarks at hand in case your slot is shortened. Keep presentations high level, but supported with more detailed information that can be added to the board books as references. Feel free to include optional reading in your documentation for board members who want to learn more. Above all, avoid the technical jargon – as discussed, presentations must be framed in terms of business outcomes and risk management. The board typically has no interest in bits and bytes – they operate at a much higher level.
Be sure to review the over-all board agenda for your presentation day – understand who else is presenting and what issues are at play so you can take the opportunity to cross-reference your remarks to other presentations. This will help reinforce your message and confirm your engagement with the board process.
Keep your schedule clear on presentation day to avoid scheduling conflicts and undue stress in case your slot gets moved, or in case you are invited to stay over a meal break for further discussions. Stay hydrated – have water before you speak, and have water available during your presentation to keep your voice full. Put your phone on silent mode! Bring copies of supporting materials, reports, and reference data so everything is at your fingertips in case questions arise. Be prepared for the “What keeps you up at night?” question – a board favourite. And be sure to bone up on the latest on cybersecurity current events – board members will feel free to come out of left field and ask your opinion of an emerging news item that they may have seen in that day’s New York Times or Globe & Mail. Your preparedness will help strengthen the board’s confidence in you.
Consider starting your presentation with a quick anecdote or recent success story by your team in defending a cyberattack. Keep this brief, but use it as a strategy to engage the audience and make the esoterica of cybersecurity “real”. You can spend an hour talking about the dangers of phishing without making an impact; showing a single example of a phishing email received by your CEO can make board members sit up in their chairs.
Good luck with your presentation!

