Social Engineering – Phone

Phone-based social engineering threats are common. This is Part III of a three-part series on the cybersecurity risks presented by social engineering. Part I: Social Engineering – Email and Phishing Part II: Social Engineering – In-Person In this era of social distancing, we’ve become more reliant than ever on technology to communicate. In this environment, social […]
Social Engineering – In-Person

In-Person social engineering threats during COVID still has us concerned. This is Part II of a three-part series on the cybersecurity risks presented by social engineering. Part I: Social Engineering – Email and Phishing In this era of social distancing, we’ve become more reliant than ever on technology to communicate. In this environment, social engineering […]
Social Engineering – Email and Phishing

Phishing is a common social engineering threat. This is Part I of a three-part series on the cybersecurity risks presented by social engineering. In this era of social distancing, we’ve become more reliant than ever on technology to communicate. In this environment, social engineering techniques are creating heightened risks from a cybersecurity perspective. Social […]
Cybersecurity and Digital Identity Management in Government

Cybersecurity and Identity Management Trends in Government The federal government continues to rely on online and digitized services. Government agencies access and process personal and other sensitive information. However, cybersecurity challenges affecting the security of critical information and infrastructure continue to be a thorn in the flesh. In a bid to ensure information security, the […]
Telecommunication and Cybersecurity

When a Teleco falls from grace, Hackers are ready to pounce. The telecommunication sector should embrace technological advancements in cybersecurity in a similar vein with the way they adopt new technologies such as 5G and the Internet of Things (IoT) in their business. In 2017, total Canadian telecommunications revenues exceeded $67 billion, with a consistent […]
World Backup Day

Backup Your Data on World Backup Day and Everyday. Tuesday, March 31 is World Backup Day! It’s an “official” day to help remind everyone about the importance of backing up your data. Having digital copies is one of your best responses to ransomware, and also puts you in a better position in case of […]
What You Need to Know about 5G
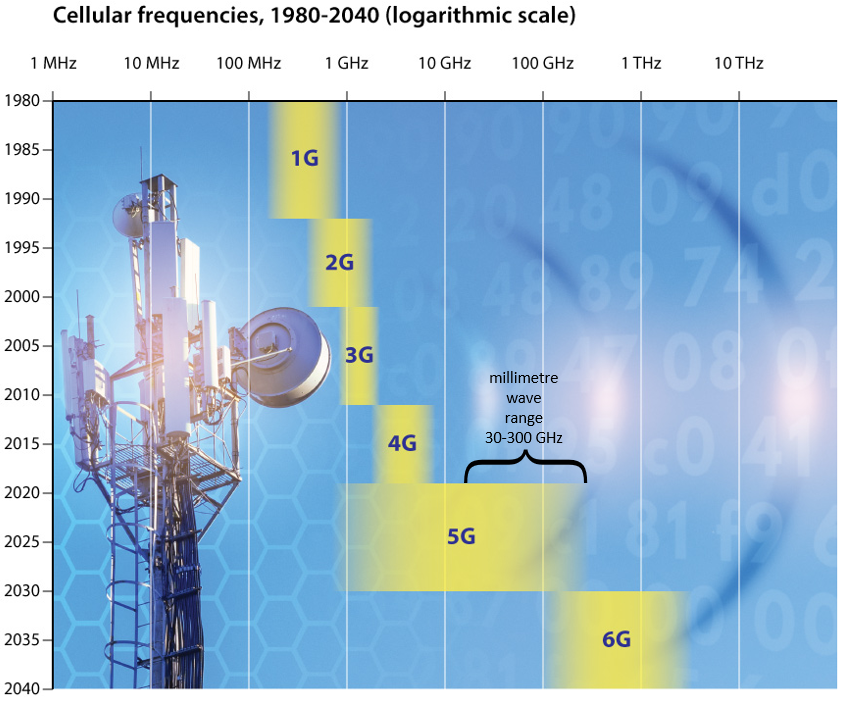
5G is the Fifth Generation of Mobile Technology 5G is the talk of the mobile world. To help make sense of the new technology, today we discuss some of the 5G terminology you may have run into lately. 5G: Let’s start really basic: 5G refers to the fifth generation of mobile technology. This generation […]
Notice to ISA’s Valued Customers During the Coronavirus / COVID-19 Pandemic

To Our Valued Customers, As the situation around the COVID-19 (coronavirus) continues to evolve, ISA has been closely monitoring the situation and we want to share some details about how our team is responding and continuing to support your business. We are collectively experiencing something that is unprecedented in the last 100 years of an […]
7 Cybersecurity Tips and Resources to Consider During the Coronavirus / COVID-19 Pandemic
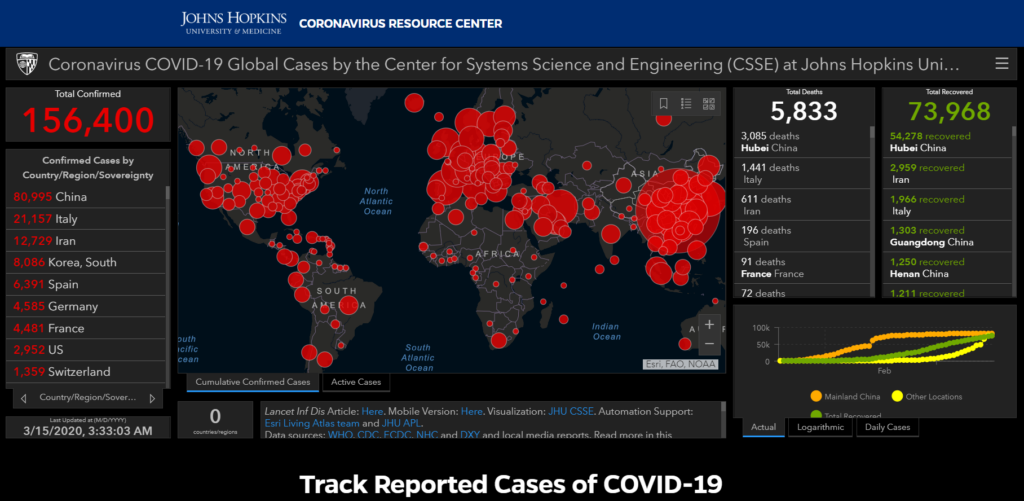
The Coronavirus/COVID-19 pandemic is here; but let’s not lose sight of staying cybersafe. By the time you finish reading this sentence, the news will have changed regarding the COVID-19 global pandemic. The spread and impact of this novel coronavirus has sent shockwaves through the world, and is likely affecting your business operations, as well. To […]
